PayPal users targeted in new SMS phishing campaign
Posted on 05.01.2021 at 12:44
A new SMS-based phishing campaign is doing the rounds that attempts to part PayPal users from their account credentials and sensitive information, BleepingComputer reports. The ploy consists of SMS text messages that impersonate the popular payment processor and inform potential victims that their accounts have been “permanently limited” and that they need to click on the link to verify their identity.
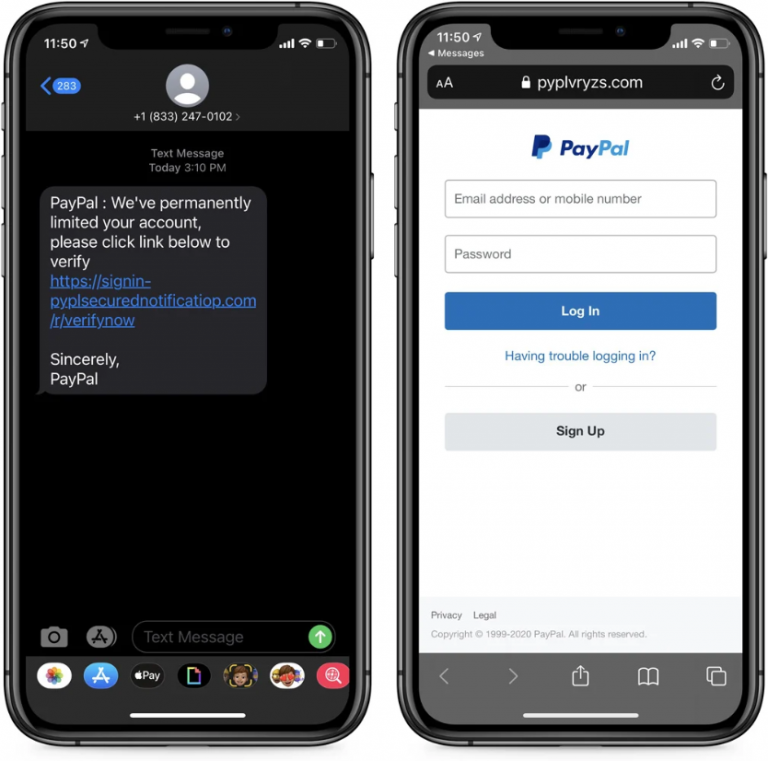
Now, at first glance the message may not seem all that suspicious since PayPal may, in fact, impose limits on sending and withdrawing money. The payment provider usually does so when it suspects that an account has been accessed by a third party without authorization, when it has detected high-risk activities on an account, or when a user has violated its Acceptable Use Policy.
However, in this case it really is a case of SMS-borne phishing, also known as smishing. If you click on the link, you will be redirected to a login phishing page that will request your access credentials. Should you proceed to “log in”, your credentials will be sent to the scammers behind the ruse and the fraudulent webpage will attempt to gather further information, including the full name, date of birth address, and bank details.
Our comments

Dr. Pavel Melnichenko
Chief Technology Officer
Typical SMS-phishing case when hackers sent links via SMS. If you click on the link, you will be redirected to a login phishing page that will request your access credentials. Should you proceed to “log in”, your credentials will be sent to the scammers behind.
Two-factor authentication will be a good adding to security in general. In case of use 2-factor authentication solutions like PayConfirm https://airome.tech/payconfirm/ for log-in, it is possible to prevent and reasonably reduce such a fraud in your digital channels.
Your clients will get used to confirm all the operations using in-app secure functions. Any attempt to make any operation using user’s credentials will generate a confirmation request on a user’s device, so such attempts will become obvious. Meanwhile, no-OTP principles of authentication process allow to perform visibility and strong integrity control checks — thus, “what you see is what you sign”
Moreover, if any malware is deployed on a smartphone of the user, this fact will be detected and provided to the anti-fraud system installed in a bank.
Impersonating the popular payment processor isn’t a novel tactic; after all, PayPal is one of the most-spoofed brands in phishing scams, and attempts at prying sensitive data out of its users have been around for years. We have previously looked under the hood of one such scheme.
Make no mistake, however; threat actors like to switch it up and use multiple flavors of PayPal fraud. While they often tend to use scamming evergreens such as lottery or prize-winning scams that require the user to pay a “transfer fee”, cybercriminals have also been observed sending out fake invoices masquerading as various charities or relief efforts. We discussed common strategies employed by scheming crooks targeting PayPal users in one of our recent articles.
Needless to say, if a target falls for any of these ruses, the combination of information could be used for identity theft, bank fraud or fraudulent purchases. The data could just as well be compiled into lists that are then sold to other scammers on dark web marketplaces. If the victim also recycles their login credentials across multiple accounts, black hats could infiltrate other accounts, including banking, social media and email accounts.
Protect yourself
To avoid falling victim to any of these attacks, you should always scrutinize any text message or email containing a link. So, if you ever receive anything suspicious purportedly coming from a service you use, contact the service provider directly and verify whether it was sent by them.
You can also never go wrong with using some form of two-factor authentication to secure your accounts. To bolster your password security, consider using a password manager.
