Depleting bank accounts and stealing identities
Posted on 25.09.2019 at 15:44
Credential stuffing has the potential to wipe out bank accounts and steal identities – and Southeast Asia is one of the biggest culprits.

A sophisticated strike where hackers use specialised software to launch multiple automatic attempts to log into a website or app using stolen usernames and passwords, the term “credential stuffing” is widely credited to Sumit Agarwal, the co-founder of cybersecurity firm Shape Security who coined it when serving as the United States’ Deputy Assistant Secretary of Defense at the Pentagon in 2010.
Stolen login details gained from data breaches or by infecting users’ devices with malware are often sold, traded or harvested for personal information and available for sale on the dark web – hidden sites inaccessible via a regular browser – where they are then used for the hundreds of millions of credential stuffing attacks which occur every day in sectors ranging from media and entertainment to retail and gaming.
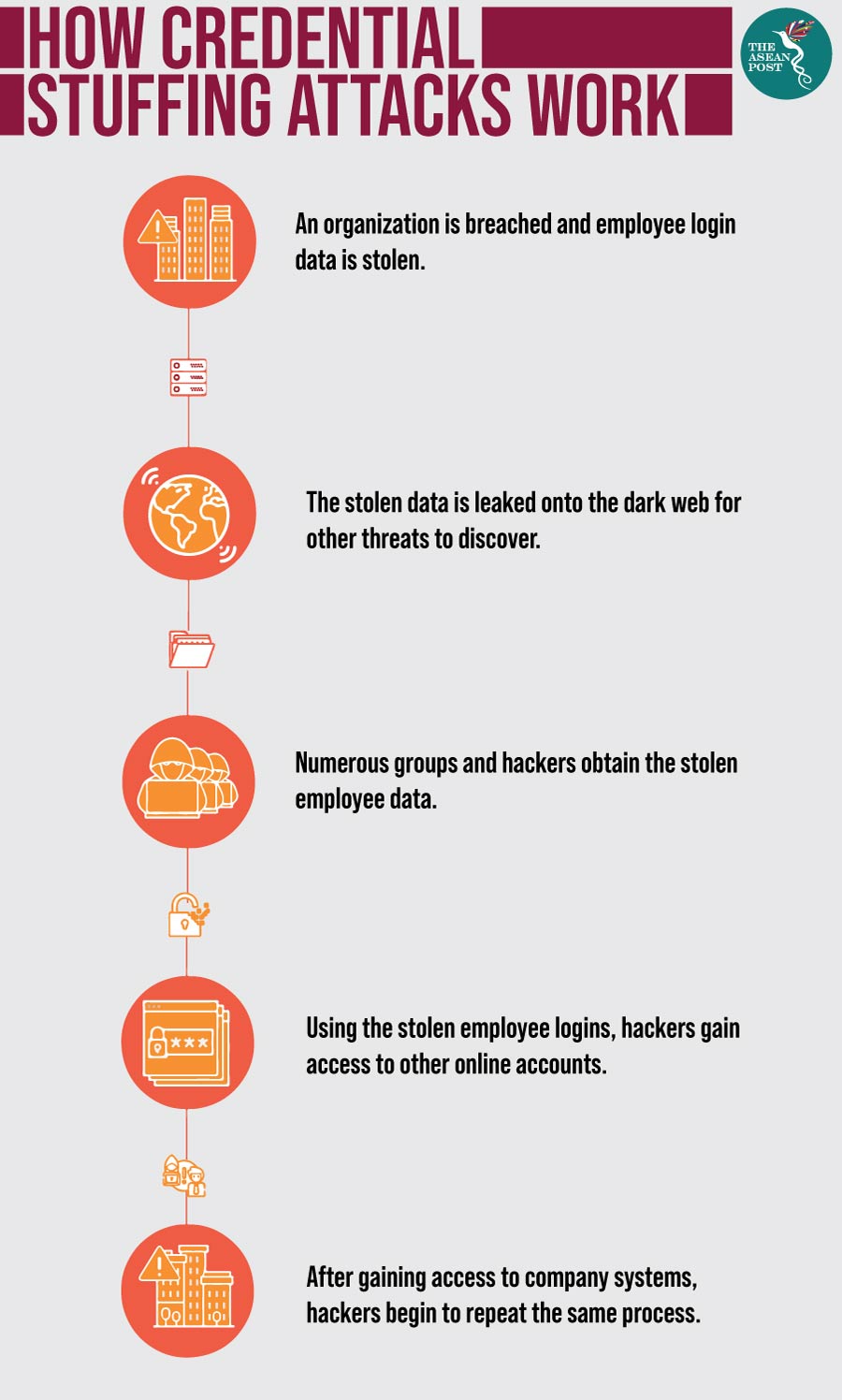
Capitalising on the fact that people tend to use the same login details across multiple websites, hackers hope the stolen usernames and passwords they have acquired for one website can then be used on others.
According to analysis by Shape Security, up to two percent of credential stuffing attacks are successful. These successful attacks can not only deplete bank accounts and credit cards but also unlock loyalty points at hotel chains and airlines, buy avatars in online games and drain the stored value in gift cards – all of which can also be resold. Such successful attacks can also lead to full-blown identity theft if social media accounts are compromised.
Our comments

Denis Kalemberg
Chief Executive Officer
Obviously, static password is the weakest way to protect any digital service. Even if your clients update passwords regulary in accrodance with your security policy and you use a secure password storage.
As a recommendation: you should focus not only on passwords’ protection but should consider to use proper 2-factor authentication.
Trying to cover the gap between passwords and real security, why don’t you turn to passwerdless & device-based authnetication?
Among a variety of authentication solutions, try to avoid any OTP-based and definietely push-codes and SMS
Read more about vulnarabilities of SMS and push: https://airome.tech/why-sms-and-push-codes-are-not-secure/
And take a look at some differences between enterprise-level and digital banking authenticvation approach https://airome.tech/payment-transaction-authentication-methods-which-is-the-best/
Five ASEAN countries – Thailand (7th), Indonesia (8th), Vietnam (9th), Malaysia (14th) and Singapore (15th) – featured in the world’s top source countries for credential stuffing from November 2017 to April 2019, a period in which cloud services provider Akamai recorded 58 billion attacks as reported in its 2019 Security Financial Services Attack Economy Report.
Malaysia was the third on the list of credential stuffing attacks against financial service organisations during the same period – behind only the United States and China.
The term “source country” designates where the traffic is coming from and does not necessarily indicate where the actual attacker is located.
Akamai noted how the gaming industry – with its commoditised items for gamers to consume such as cosmetic enhancements, special weapons or other related items – is a popular target for credential stuffing attackers. Vietnam ranked fourth globally as an attack source country on the gaming industry in the 17 months prior to April 2019, during which Akamai recorded 12 billion credential stuffing attacks on the sector.
With data breaches increasingly in the news, and many companies seemingly unaware or unwilling to disclose the full consequences of such leaks, Akamai’s Head of Security Technology and Strategy (Asia Pacific), Fernando Serto, said it is crucial that the public educate themselves of the dangers that credential stuffing pose.
“Awareness about cybersecurity is high (in ASEAN) but knowledge on credential abuse is still low,” Serto told The ASEAN Post.
“Many are not aware that there are malicious login attempts targeted at sites and a process whereby hackers are constantly exploring other avenues to exploit and mine data to commit fraud,” Serto added.
Recent data breaches
Data breaches are closely linked to credential stuffing, and the rise of data breaches in ASEAN should be a greater cause for concern. Three of the world’s largest credential stuffing attacks against streaming services last year took place shortly after reported data breaches, indicating hackers were likely testing stolen credentials before selling them.
Last week alone saw two high-profile data breaches dominate regional headlines.
In Indonesia, the communications ministry said it was probing a data leak at two of Lion Air’s subsidiaries, Malaysia-based Malindo Air and Thai Lion Air, after passenger data of up to 35 million customers was reportedly stolen from remote servers operated by Amazon and posted for sale on the dark web.
In Malaysia, the country’s health ministry was scrambling to investigate a claim by German security firm Greenbone Networks that the radiological reports of nearly 20,000 Malaysians were freely accessible on computer servers worldwide.
Meanwhile in July, international beauty retailer Sephora announced that personal details of its online customers in Indonesia, Malaysia, the Philippines, Singapore and Thailand and were among those to have been leaked after a data breach. Users on the dark web were later found to be selling usernames and passwords of 500,000 users of Sephora’s Indonesia and Thailand websites.
Regulators are clamping down hard on data breaches, and Singapore’s Personal Data Protection Commission (PDPC) has issued fines of over S$1.28 million (US$929,600) this year alone – more than the total amount of fines over the past three years. Among those who were fined – mostly for failing to implement reasonable security measures to protect personal data in its possession or control – include IT vendors Integrated Health Information Systems, healthcare providers SingHealth and firms such as GrabCar, AIA and COURTS.
Recommendations
To safeguard themselves, Serto recommends the public to change their passwords on a frequent basis and ensure that it is made up of different characters. Websites that do not offer a multi-faceted authentication (hardware/software) should also be avoided.
Companies, meanwhile, need to have solutions in place which can detect highly suspicious, automated activity and separate human versus automated users.
Credential stuffing isn’t going anywhere, and since it cannot be stopped outright, the goal should be making the process of obtaining credentials as difficult as possible.
As Martin McKeay, a security researcher and editorial director at Akamai noted, weak passwords and password reuse are the bane of account security in every industry.
“If a password is weak or reused across multiple accounts, it will eventually be compromised,” he warned.
by The ASEAN Post
Reference: https://theaseanpost.com/article/depleting-bank-accounts-and-stealing-identities.
