Op Wocao – China-linked APT20 was able to bypass 2FA
Posted on 23.12.2019 at 15:50
Security experts from cyber-security firm Fox-IT warns of a new wave of attacks, tracked as Operation Wocao, carried out by China-linked cyber espionage group APT20 that has been bypassing 2FA.
The attacks aimed at government entities and managed service providers (MSPs) that were active in many industries, including aviation, healthcare, finance, insurance, energy, and gambling.
The APT20 group has been active since at least 2011, but experts did not associate any campaign with this threat actors between 2016 and 2017.
Over the last two years, the group targeted government and large corporate networks by attempting to exploit vulnerabilities in the JBoss open-source application server.
“Operation Wocao (我操, “Wǒ ”, used as “shit” or “damn”) is the name that Fox-IT uses to describe the hacking activities of a Chinese based hacking group.” reads the report published by Fox-IT.
“In several cases the initial access point into a victim network was a vulnerable webserver, often versions of JBoss. Such vulnerable servers were observed to often already be compromised with webshells, placed there by other threat actors. The actor actually leverages these other webshells for reconnaissance and initial lateral movement activity. “
Our comments

Dr. Pavel Melnichenko
Chief Technology Officer
An exciting case that proves again that OTP-tokens can be techcnically bypassed even if they were developed by big brands.
Unlike standard OTP-based tokens, PayConfirm uses several components, including private key, to generate a signature. To get access to the private key, one should provide a secrete. Without teh private key unlock it will not be possible to confirm operations.
Another interesting point about PayConfirm, that makes it different from OTP-based token, is the use of exact operation details to generate a digital confirmation. Thus, every operation goes through integrity control checks.
As the result, it is impossible to generate any confirmation without the signer that knows the secret to unlock the key on one hand, and with strong intergrity control checks it’s impossible to persuade the client to sign any starnge operations as what you see is what you sign.
Once the hackers have gained access to these servers, they will deploy web shells for reconnaissance and lateral movements.
In order to move laterally within the target networks, hackers used well-known techniques, such as dumping credentials from memory and accessing password managers on compromised systems.
Attackers use stolen VPN credentials to securely connect the target network. According to the experts, the threat actor has been able to stay under the radar even using simple tools and techniques for their hacking campaigns.
Fox-IT noticed that the APT20 group was able to abuse VPN accounts that were protected by 2FA, the experts believe that the group devised a specific technique to achieve this goal
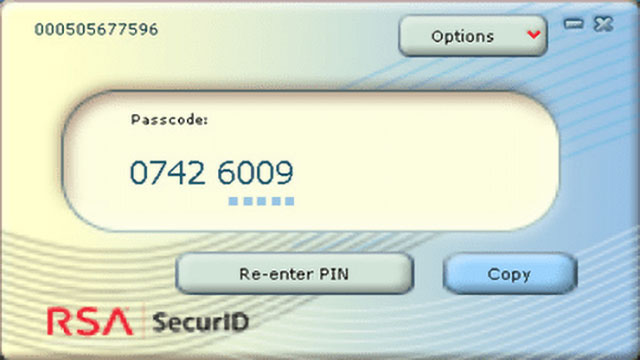
They speculated that the APT20 group stole an RSA SecurID software token from a compromised system, then used it on its systems to generate valid one-time codes and bypass 2FA.
“An interesting observation in one of Fox-IT’s incident response cases was that the actor steals a softtoken for RSA SecurID, which is typically generated on a separate device, such as a hardware token or mobile phone.” continues the report. “In this specific case however, victims using the software could also use a software based token to generate 2 factor codes on their laptop. This usage scenario opens up multiple possibilities for an attacker with access to a victim’s laptop to retrieve 2 factor codes used to connect to a VPN server”
Conclusion
Anyway, the software token must be generated for a specific system, the threat actors were able to do it by retrieving information once inside the target network.
“As it turns out, the actor does not actually need to go through the trouble of obtaining the victim’s system specific value, because this specific value is only checked when importing the SecurID Token Seed, and has no relation to the seed used to generate actual 2-factor tokens. This means the actor can actually simply patch the check which verifies if the imported soft token was generated for this system, and does not need to bother with stealing the system specific value at all.” continues the experts.
“In short, all the actor has to do to make use of the 2 factor authentication codes is to steal an RSA SecurID Software Token and to patch 1 instruction, which results in the generation of valid tokens.“
by Security Affairs
Reference: https://securityaffairs.co/wordpress/95536/apt/apt20-op-wocao.html
